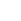According to the relevant laws and regulations of mainland China, you can only use social acceleration after passing real-name authentication.

According to the relevant laws and regulations of mainland China, you can only use social acceleration after passing real-name authentication.According
to the relevant laws and regulations of mainland China, you can only use social acceleration after passing real-name authentication.

[Security Guide] Beyond Acceleration: Can Using an Accelerator Also Protect My Privacy?
#Beginner's Guide
The answer is:
Yes, but the premise must be clear—its main function is to optimize the network, and privacy protection is an important "derived benefit".
Let's understand this with a simple analogy.
Without Protection: Your Network Activity is Like "Postcards"
Under normal network conditions, especially on public Wi-Fi, your data is like postcards. All intermediate parties (such as your network operator, Wi-Fi provider) can
potentially see which websites you visit and what data you send (although the content is encrypted if HTTPS, the destination is visible).

With Accelerator: Your Data Enters an "Encrypted Tunnel"
When you start the accelerator, it establishes an encrypted dedicated tunnel between your device and our acceleration server.
1. Encrypt Content: All your network data (including destination and content) is strongly encrypted before entering the tunnel, turning into gibberish. For any
intermediate party, this data becomes unreadable.
2. Hide Destination: Your network requests are first sent to our acceleration server, then the server accesses the target website on your behalf. Therefore, from your
local network operator's perspective, you are only communicating with our server, and
they cannot know which game or website you ultimately accessed.
What Can It Defend Against? What Can't It Defend Against?
Protection it can provide:
- Defend against public Wi-Fi eavesdropping: Prevent hackers from stealing your data in cafes and airports.
- Hide browsing history from ISP: Hide your real access targets from your network operator.
- Bypass local network restrictions: Help you access services blocked on campus/corporate networks.
Protection it cannot provide:
- Defend against viruses/malware: Cannot prevent malicious software on your device from stealing information.
- Prevent website tracking: Cannot prevent websites from identifying you through cookies, fingerprinting, and other technologies.
To summarize: Using a trustworthy accelerator is like hiring a "confidential messenger" for your network communication. It not only takes you on a faster route but also
ensures your message content is not spied on during transit.





 service@speedx.link
service@speedx.link